AdoptIWF
(Log Management)
Organize and Mediate
Any Device, Any Network
Any Vertical
Scale your existing Core System flexibly to provide end-to-end Log Management Solution
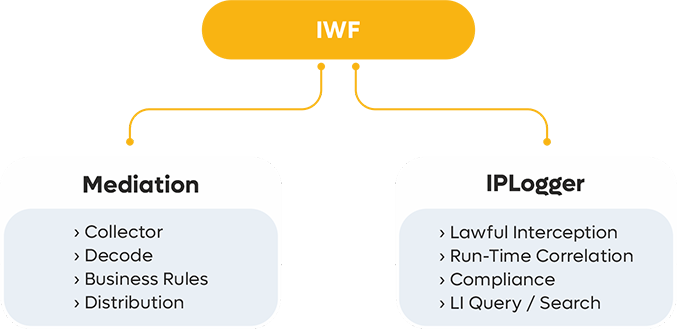
Adopt IWF System collects, stores, correlates and analyses large volume of network and security event logs for security, auditing and reporting purpose. Log information is immediately available for near real-time security investigations and incident response. It provides end-to-end IP details and subscriber details based on Public/Private IP, MSISDN, BNG IP and Cell ID, etc.
Adopt IWF is also a convergent mediation to process large amount of CDRs and send them to downstream systems like BSS, FMS or RA.
IWF Architecture
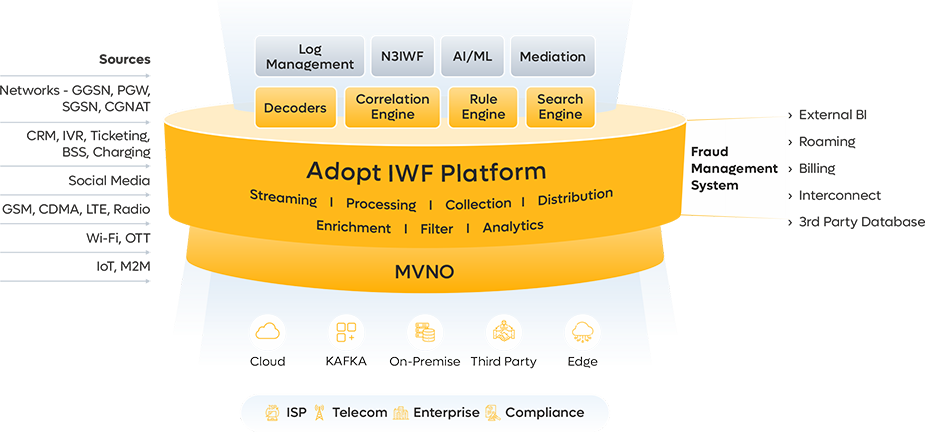
Adopt platform is based on microservices architecture which can be deployed at edge, which works in coherence with our distributed cloud controller architecture based on Enterprise need of Security, Regulatory Compliance, Scalability, Network Latency, Maintenance and Troubleshooting.
Key Features
IWF Key Benefits:
Carrier Grade Reliability and Proven Performance
Investigation teams and vigilance authorities can easily achieve complete information of users
Improved security through a reduced attack surface, real-time monitoring and improved detection and response times
Ease in operations – Reduced severity of business interruptions
Improved observability and visibility across the enterprise through a common event log
Flexibility in search logic, ensuring faster search results
Provides capability to filter, analyze and generate reports based on log messages
Optimum and unified storage for huge data traffic supporting millions of PDP sessions
Manage long-term Log data storage in database file system for over a year
Highly customized Software Application based solution
Faster and more precise troubleshooting capabilities through advanced network analytics
Key Highlights:
Easy Integration:
Easy integration with standard network elements with no additional cost incurred
Scalability:
99.9999% availability of live use cases with horizontal and vertical scalability
Microservices Architecture:
A pluggable and modular architecture with fault tolerance and high availability
Cloud Native Solutions:
With support of Docker and Kubernetes, IWF automates the process of DevOps
Distributed Architecture:
Collection service at different sites and processing at central site to save cost
Easy Management:
Faster and risk free deployments and upgrades on single and / or multiple microservices
Faster Implementation:
Single site IPLogger solution implementation can be done in 2 days in-turn assuring cost effective implementation TAT